How I earned $800 for Host Header Injection Vulnerability
HTTP response header injection vulnerabilities arise when user-supplied data is reflected into a response header in an unsafe way.
The host header specifies which website or web application should process an incoming HTTP request. Host header attack possible, an attacker can manipulate the Host header as seen by the web application and cause the application to behave in unexpected ways.
The Host header determines which site an web application should process an approaching HTTP request.
They pose many risks and induce various attack vectors namely
⦁ password reset poisoning / invite feature poisoning
⦁ cache poisoning
⦁ access to other internal host/application
⦁ XSS, etc.
TIP
If the website works with an arbitrary host header, the client can modify the host header to contain anything. This can introduce a security issue if the host header is then used within the application.
Attack Scenario:
⦁ The attacker sends a reset password request to another user by modifying the Host Header in the request with any malicious site.
⦁ The user receives an email to reset the password, clicks the link and proceeds further with the malicious link.
⦁ By this way, an attacker can obtain valid password reset token for any user.
I found this vulnerability on a private program on Bugcrowd platform. I started to test for vulnerabilities such as XSS, CSRF, etc. Interestingly the application accepts arbitrary Host Header and so I decided to test for Cache Poisoning on the Password reset endpoint.
I’ve explained below on how to reproduce Host Header Injection to poison the Password Reset link and to take over accounts.
Writeup
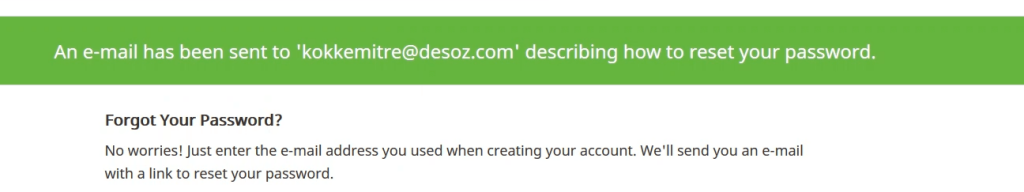
The password reset page looks like this.
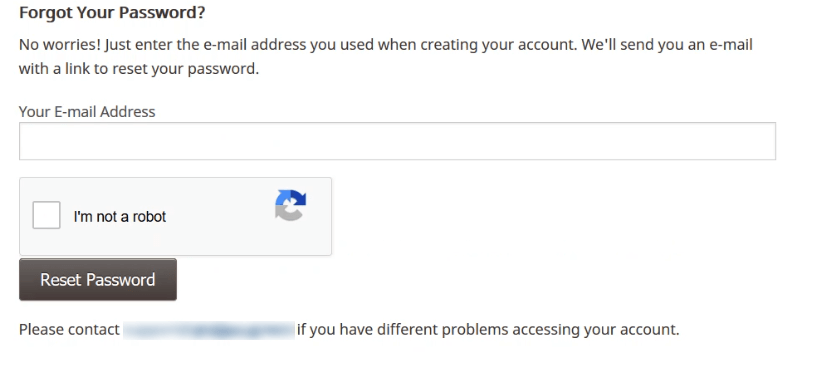
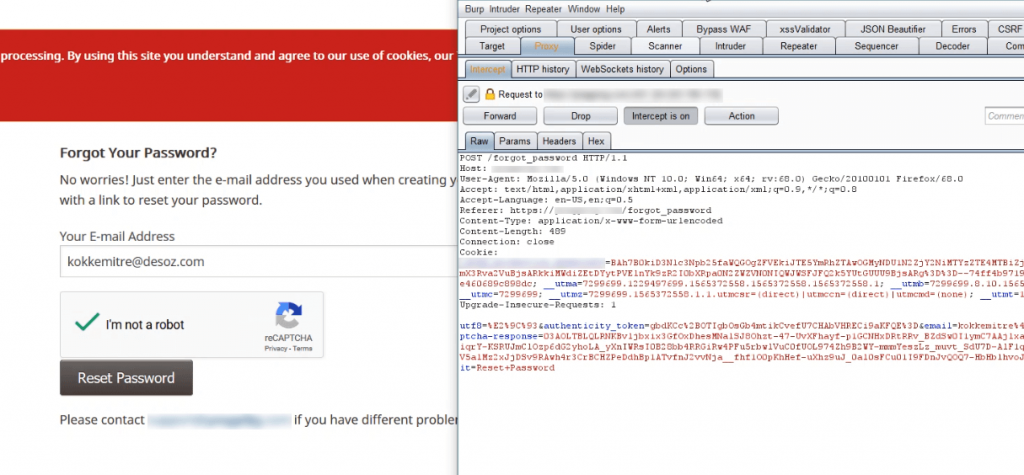
Now, just type the email to reset the password and fire up Burp Suite to intercept the traffic and click Reset Password.
Now on the Burp Suite, capture the request and change the HTTP Request Header Host parameter from the original URL to any site you wish. I’ve used google.com as example below.
Now when you analyse the above screenshot, the Host header is changed to a malicious site, forward the request and when the request been passed, the attack triggers.
An email containing the password reset link will be sent to the user.
As you can see, the received password reset link has been sent containing the Poisoned password reset link.
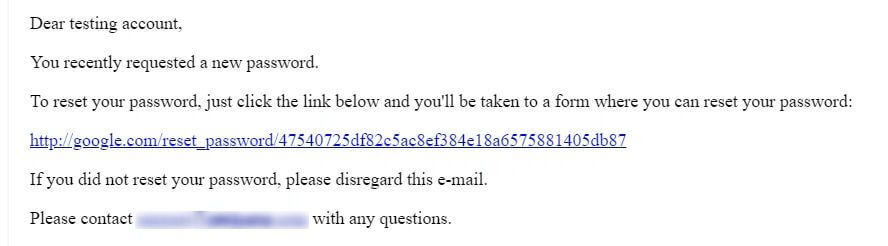
This allowed me to steal the user’s password reset token.
For reporting this vulnerability sensibly, I’ve been awarded with $800 💰
References:
https://portswigger.net/kb/issues/00200200_http-response-header-injection
https://www.acunetix.com/blog/articles/automated-detection-of-host-header-attacks/
Thanks for reading this article. Stay tuned for more Bug bounty & Pentesting tutorials!
You may like

How to use Burp Suite Like a PRO? PART – 2